How to identify and report a phishing email
Instructions
Q1. How do I identify a phishing email?
The intent of a phishing message is to steal information from a person. This is done by sending a message that looks authentic and deceiving the recipient into divulging their personal information such as usernames, passwords, and financial information.
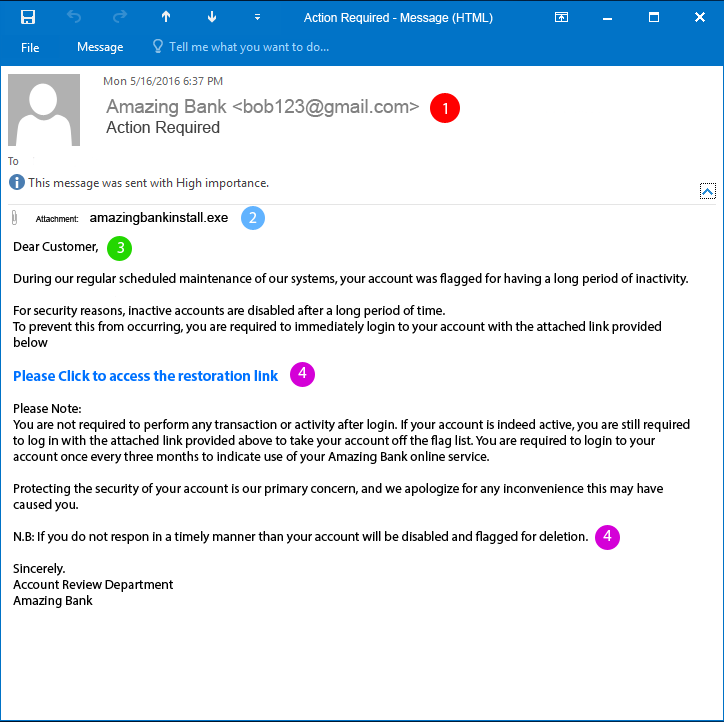
Here is an example of a phishing email with four common characteristics identified:
The message comes from an unknown sender. Many times these messages give the false impression that they are coming from a known source. However, upon closer inspection, the sender’s email address is not associated with the person or entity that they claim to be.
The message will contain an unsolicited attachment. Opening these attachments can be harmful to your computer and your information. If you receive a message with an attachment that you did not request, do not open the attachment.
Generic or no greeting. Most reputable and well-known companies will address you professionally and by your name. If you receive a message claiming to be from your bank and it greets you with “Hey Customer” or even “Dear Customer” then you should be on alert.
Threats & Links – The message may include a threat to instill a sense of urgency to take action immediately — for example, your account will be closed if you do not click on the link and verify your information.
An email that is poorly written can also be a sign of a phishing email. Some messages, however, will be difficult to identify as they look professional and appear to be from a well-known business or entity, including UCLA. Our UCLA IT Security department maintains a running list of phishing emails that have been reported in the wild. Please click here to see the list.
Q2. How do I report a phishing email?
When you receive a phishing email, you should report it directly to UCLA IT Security (they are the head IT unit at UCLA in charge of security on campus) by doing the following:
Provide a full copy of the email by “saving” the email within your email client.
– For Microsoft Outlook users, this can be accomplished by hitting File > Save As after opening the email.Compose a new email with the previously-saved phishing message added as an attachment.
Send the resulting message and attachment to security@ucla.edu with a subject line identifying the message as a phishing report.
Lastly, mark the message as junk and delete the email.
For more detailed instructions on how to save the email in Windows, Mac, or Gmail, please visit IT Security’s website here.
Q3. Can I be phished on my phone over text messages?
Yes, phishing scams are not only isolated to email but they are the most common. If you receive a suspicious request from an unknown number then ignore it or reach out to the person whom they are impersonating.
If you have any questions about an email you received, need assistance in reporting, or other general assistance, please contact the HumTech Service Desk. We are here to help!
https://ociso.ucla.edu/phishing-scams/instructions-reporting-phishing-scam